This new SSL / TLS attack nick named FREAK actually exploits deliberately weak “export ciphers” push by the NSA more than a decade ago.
These ciphers were deliberately made weak so that the US Government could decrypt the traffic.
Export cipher suits such as EXP-DES-CBC-SHA are vulnerable to the attack. In my earlier post regarding SSL best practices I have added the following in my OpenSSL config. So if you used this config FREAK should not be a concern.
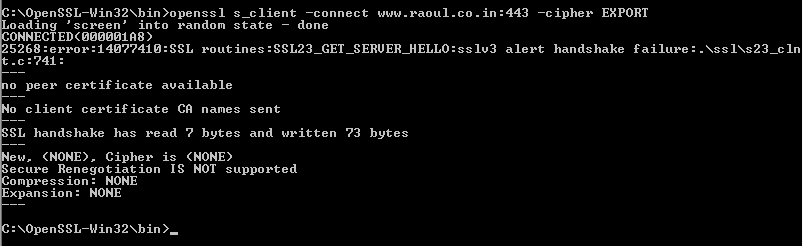
To test your current server you can use the OpenSSL tool kit for Windows and run this following command.
# openssl s_client -connect www.raoul.co.in:443 -cipher EXPORT
If any export ciphers are disabled, you will see a similar error.
Have something to add?